The Importance of IT Security
In our rapidly-evolving digital age, IT security is more important than ever. As technology becomes increasingly integrated into our daily lives and business operations, so too do the risks of cyber threats and attacks. IT security is not just about protecting our personal information, but also about ensuring our safety, privacy, and trust in the digital world.
IT security refers to the policies, practices, and tools that aim to prevent, detect, and respond to cyber threats and attacks. Cyber threats and attacks are malicious attempts to compromise or damage data, systems, networks, or devices. They can come from a variety of sources, including hackers, criminals, terrorists, competitors, or even insiders. Cyber threats and attacks can have a variety of motives, such as stealing data, extorting money, disrupting services, sabotaging operations, or influencing opinions.
IT security is a complex and ever-changing field. It involves many different aspects, such as physical security, network security, application security, data security, identity and access management, encryption, firewalls, and antivirus software. It also involves many different people, such as users, developers, administrators, managers, auditors, and regulators. A holistic and proactive approach to IT security is essential, taking into account the risks, costs, benefits, and trade-offs of different solutions.
Why is Tech Security Important?
Guarding Personal and Business Assets:
- At the most fundamental level, tech security safeguards personal and business assets. A lapse can mean loss of sensitive data—be it personal details, proprietary business information, or financial credentials.
Preserving Reputation and Trust:
- Breaches and attacks not only cause financial damage but can significantly dent the reputation of businesses. Trust, once lost, can be challenging to rebuild.
Economic Implications:
- From a broader perspective, cybercrimes have vast economic implications, with billions being lost annually. Proper IT security can help mitigate these losses.
Legal and Compliance Reasons:
- Various jurisdictions have regulations to ensure data protection. Businesses must be compliant, or they face penalties. Effective tech security aids in meeting these standards.
What are the Important Aspects of IT Security?
IT security is a broad term that encompasses all the measures that an organization takes to protect its information assets from unauthorized access, use, disclosure, disruption, modification, or destruction. The important aspects of IT security can be divided into two categories:
- Preventive measures: These measures are designed to stop attacks from happening in the first place. They include things like authentication, authorization, encryption, firewalls, and regular updates.
- Reactive measures: These measures are designed to deal with attacks that do happen. They include things like incident response procedures and disaster recovery plans.
Here is a more detailed explanation of each of the important aspects of IT security:
- Authentication: Authentication is the process of verifying the identity of a user or system. This is typically done by requiring users to provide something they know (like a password), something they have (like a security token), or something they are (like a fingerprint).
- Authorization: Authorization is the process of granting users the permissions they need to access specific resources. This is typically done by assigning users to roles, which define the permissions that they have.
- Encryption: Encryption is the process of converting data into a code that can only be decrypted by authorized users. This is a powerful tool for protecting data from unauthorized access.
- Firewalls: Firewalls are devices that filter traffic between networks. They can be used to block unauthorized traffic from entering a network.
- Regular updates: Keeping systems and software up to date is important for security. Software updates often include security patches that fix vulnerabilities that could be exploited by attackers.
- Incident response: Incident response is the process of dealing with security breaches when they occur. This includes things like isolating the affected systems, investigating the incident, and notifying affected parties.
By implementing the important aspects of IT security, organizations can protect their information assets from a variety of threats. This will help to ensure that their business operations are not disrupted and that their sensitive data is not compromised.
What are the 3 Key Concepts of IT Security?

The CIA triad is a framework for understanding and managing information security that first appeared in the 1970s. It is based on three foundational concepts: confidentiality, integrity, and availability. It is still relevant today, and it is the foundation of many information security frameworks and best practices.
- Confidentiality means ensuring that data is accessible only to those who have the right to view it. This is important to protect sensitive data, such as financial information, personal identifiable information (PII), and trade secrets.
- Integrity means ensuring the accuracy and reliability of data and systems. This is important to ensure that data is not modified or corrupted without authorization.
- Availability means making sure that systems and data are accessible when needed. This is important to ensure that businesses can continue to operate and that individuals can access the information they need.
The CIA triad got its name from the first letters of each of the three concepts. It is often used as a mnemonic device to help people remember the three key aspects of information security. Cyberattacks are becoming more sophisticated, and they are targeting a wider range of organizations.
Imagine that you have a box that can store information. You can put anything you want inside the box, but only you have the key to open it. No one else can see what’s inside the box unless you let them. This is what confidentiality means in IT security. It means that your data is protected from unauthorized access or disclosure.
Now imagine that you have a friend who also has a box that can store information. You decide to exchange some information with your friend, so you both put something inside your boxes and lock them. Then you swap the boxes and use your keys to open them. However, when you open your friend’s box, you find that the information inside is different from what your friend told you. Someone has changed the information without your friend’s knowledge or permission. This is what integrity means in IT security. It means that your data is accurate and reliable, and has not been modified or corrupted by unauthorized parties.
Finally, imagine that you have a box that can store information, but it is very heavy and hard to move. You want to access the information inside the box, but you can’t because the box is stuck in a place that is far away or difficult to reach. You also can’t open the box remotely or send the information to yourself. This is what availability means in IT security. It means that your data and systems are accessible and usable when you need them, and are not affected by disruptions or failures.
What are the 5 Principles of IT Security?

The 5 principles of IT security concept emerged in the early 1970s, when the first computers were being used in businesses and organizations. At the time, security was not a major concern, as computers were not as widely used and the threats were not as sophisticated. However, as computing became more widespread, it became clear that security was essential to protect data and systems from unauthorized access, modification, or destruction. (Bishop, 2002, Computer Security: Art and Science. Addison-Wesley Professional)
The 5 principles of IT security were developed to provide a framework for organizations to follow in order to protect their information assets. They are:
- Layered defense (defense in depth): This principle states that you should have multiple layers of security in place to protect your systems and data. This way, if one layer fails, the others will still protect you. For example, you might have a firewall to protect your network from unauthorized access, antivirus software to protect your devices from malware, and strong passwords to protect your accounts.
- Least privilege: This principle states that users should only have access to the resources they need to do their job. This helps to protect your systems and data from unauthorized access. For example, you might give an employee access to a specific file or folder, but not to the entire network.
- Separation of duties: This principle states that key tasks should be divided among different people to prevent fraud and errors. This helps to ensure that one person cannot do something malicious or make a mistake that could damage your systems or data. For example, you might have one person approve invoices, another person pay them, and a third person reconcile the accounts.
- Need to know: This principle states that data should only be accessible to those who need it to do their job. This helps to protect sensitive data from unauthorized access. For example, you might only give employees access to customer data that they need to do their job.
- Regular audits and monitoring: This principle states that you should regularly audit your systems and data to ensure that they are secure. You should also monitor your systems for potential threats. This helps to identify and fix security vulnerabilities before they can be exploited.
The 5 principles of IT security are still relevant today, and they form the foundation of many IT security frameworks and best practices. By following these principles, organizations can help to protect their information assets from a variety of threats.
What are the Four Types of IT Security?

The concept behind the four types of IT security is that different threats require different security solutions. For example, network security is designed to protect against unauthorized access to a network, while endpoint security is designed to protect individual devices from threats.
- Network security: Network security protects against unauthorized intrusion and misuse of resources within the network. This can include firewalls, intrusion detection systems, and data encryption.
- Endpoint security: Endpoint security focuses on ensuring individual devices (like computers and smartphones) are free from threats. This can include antivirus software, anti-malware software, and patch management.
- Cloud security: Cloud security addresses challenges related to protecting data, applications, and infrastructures in cloud environments. This can include encryption, access control, and vulnerability scanning.
- Application security: Application security secures software applications against malicious threats and vulnerabilities. This can include code review, penetration testing, and security testing.
What are the 7 P’s of Information Security Management?
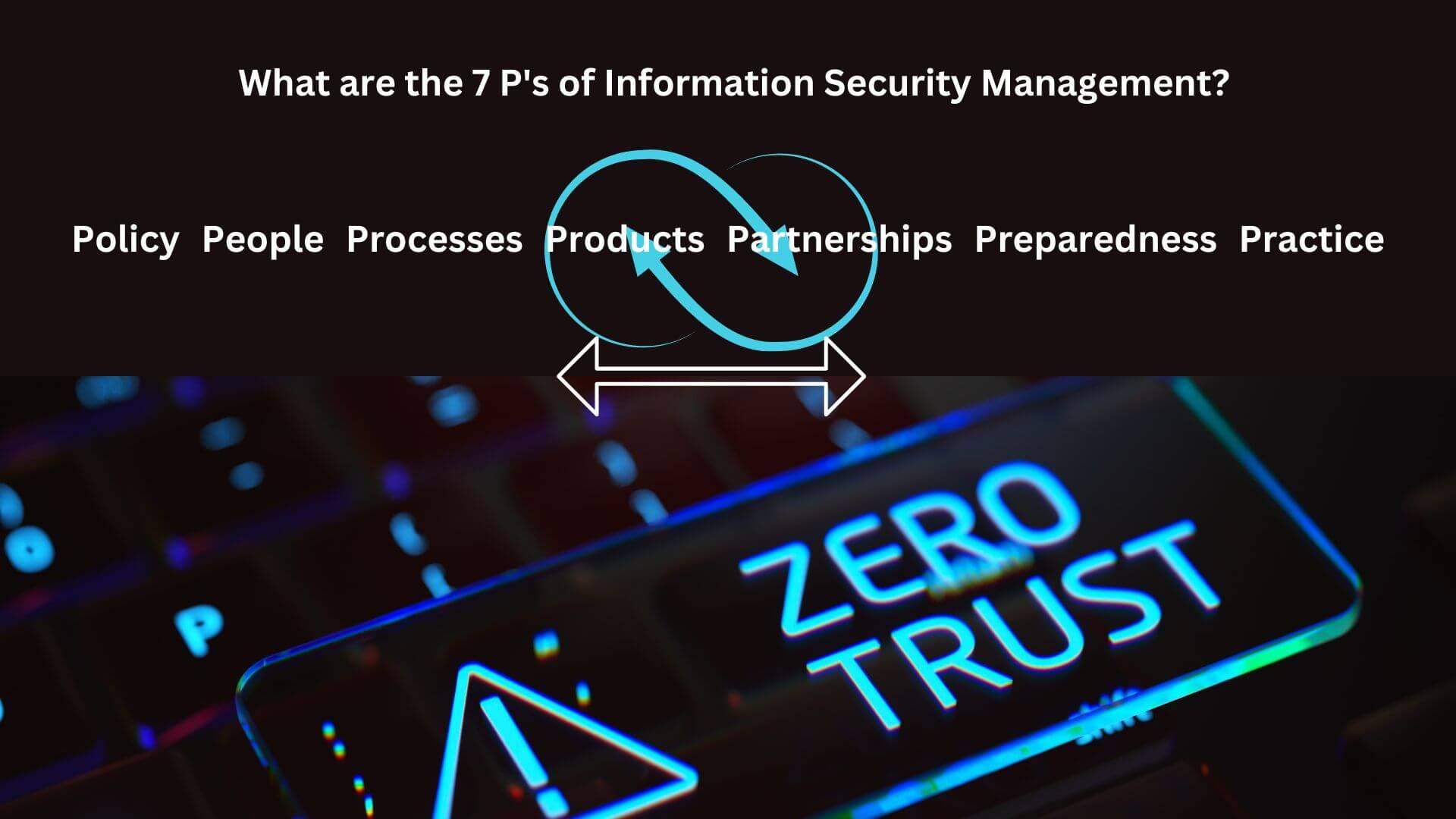
The 7 P’s of Information Security Management concept began in the early 2000s, as organizations began to realize the importance of information security. Information security management is the process of protecting an organization’s information assets from unauthorized access, use, disclosure, disruption, modification, or destruction. It is important for organizations of all sizes, regardless of the industry they are in. (Alexander, D., Finch, A., Sutton, D., & Taylor A. (2013). Information Security Management Principles. BCS Learning & Development Limited)
Information security management is about protecting the information that an organization uses to conduct its business. This information can include anything from customer data to financial records to intellectual property.
- Policy: This is the foundation of your security program. It should define your security goals and objectives, and it should be supported by senior management.
- People: Your employees are your first line of defense against cyberattacks. They need to be trained on security best practices and they need to be aware of the risks.
- Processes: Your security processes should be well-defined and documented. They should be reviewed and updated regularly to ensure that they are effective.
- Products: You need to use security products that are appropriate for your organization’s needs. These products should be properly configured and maintained.
- Partnerships: You need to partner with other organizations to share information and resources. This will help you to improve your security posture.
- Preparedness: You need to be prepared for a cyberattack. This includes having a plan for responding to an attack and having backups of your data.
- Practice: You need to practice your security procedures regularly. This will help to ensure that your employees are familiar with them and that they can be executed effectively in the event of a cyberattack.
In simple terms, the 7 P’s of Information Security Management are a framework for creating a secure organization. They focus on the human element, the technology element, and the process element of security. By following these principles, you can improve your organization’s security posture and protect your sensitive data from cyberattacks.
Conclusion
The importance of IT security can never be overstated. As we lean more on digital platforms and tools, fortifying our technological fronts becomes imperative. Through understanding and implementing foundational concepts, principles, types, and the 7 P’s, individuals and businesses can navigate the digital space with more confidence and security. As cyber threats evolve, so must our strategies and understanding. Prioritizing IT security isn’t just an option—it’s a necessity, and Zeren Software, along with a dedicated team of experts and professionals in digital trust and cyber security, can make it happen.








